Crypto Machines
© Brooke Clarke,
N6GCE 2002 - 2024
M-94
25 wheel Cipher Device (Wiki)
M-94 is the U.S. Army nomenclature, CSP-488 is the
Navy name.
The M-138-A is a strip cipher version.
The Jefferson Disk (Wiki)
aka: Bazeries Cylinder (Wiki)
works on the same idea, but is much older.
Manual operation. Simple construction.
Used through the end of W.W.II.
Enigma
Got the crypto bug from reading The Ultra Secret by F.W. Witherbotham.
It told about breaking the Enigma machine. I've wanted one
of these since then (1975) but real machines are very
collectable (expensive) so never got one. Did get the Enigma-E
kit to make a functional machine, but it does not have the
look and feel of a real machine. The Enigma I shown here
is a non functional machine that does have the look and feel of
a real enigma machine.
This came from Spain. Maquina Enigma - This is
the Enigma I model.
White Collar TV series (Wiki,
IMDB): S2-E16
"Under the Radar" booby trapped Nazi Submarine & Enigma
Machine - Preview@0:20
-
The movie "In Enemy Hands", 2004 (IMDB, Wiki)
has a short
scene showing an Enigma working. (does not show rotors)
Fig 1 Spain to California took it's toll,
But no damage to Enigma.
2024Feb6: will improve.

|
Fig 2
 |
Fig 3
 |
Fig 4
 |
Fig 5 Rotor cover hinges open
 |
Fig 6
 |
Fig 7
 |
Fig 8 Inside Lid

|
|
GRA-71
Coder-Burst Transmission Group (British GRA-71 for
the PRC-316)
Magnetic tape holds a short message that is sent using
300 Word Per Minute Morse code (Burst transmission (Wiki).
Can be used with the GRC-109,
PRC-64, Delco
5300, PRC-74, PRC-316, PRC-319, PRC104
& probably most modern radios that support CW operation.
Manual operation.
Used through Vietnam conflict.
Voice
Used with the PRC-68 Family
of hand held Squad Radios, Digital 16
kbps
Should inter operate with the KY-57
(ground) and KY-58 (airborne) systems
Post Viet Nam.
VINSON (Wiki)
voice encryption system (Wiki)
Works with the PRC-77 but
not the PRC-25. Mechanical key
loading.
Should inter operate with the KY-8 (Vehicular) and KY-28
(airborne)
Used through Viet Nam.
NESTOR system replaced by VINSON.
Used with a large number of radios for both voice, fax
and data.
Late Vietnam.
VINSON system (Wiki)
Used with PRC-104 and other H.F.
radios.
? mid to late Vietnam (same box as PRC-25 and PRC-77)
Parkhill system.
Not much is known.
What encryption system, what will it interoperate with? Let me know.
Wiki:
ANDVT,
Replaces the KY-57 and other equipment. Requires new
interconnecting cables.
Uses a 40 character key based on 5-level paper
tape. Originally designed to work with the PRC-77.
Uses thumb-wheel switches to set key.
Should work on any radio via audio input & output.
GPS
Key loaded from KYK-13.
DAGR
AN/PSN-13()
Has an Over The Air Rekeying (
Wiki)
capability and individual serial number.
There may be a shut down function that works by unit serial
number.
PLGR
AN/PSN-11 GPS Receiver
Can use a crypto key for reception
of the GPS L2 frequency.
Can use a crypto key for reception
of the GPS L2 frequency.
Version of the Trimpack that
decodes encrypted L1 to avoid problems when SA was turned on.
Requires key load for encrypted signals but works as civilian
receiver without keys.
Analog Data
An aircraft module for encoding and decoding digital to
analog. Probably no crypto function although nomenclature is
KY-...
Digital Data
There are a large number of crypto
boxes used to encrypt/decrypt teletype transmissions. This
is the most common digital data application.
FS-5000
FS-5000 Spy Radio, uses I&Q
modulation for Tx and Rx. Most likely that the missing
control box contains some type of encryption that would allow the
spy to compose a message in the field and send it as well as
decrypt an incoming message. This would require inputting a
key. If the missing control box did not contain any crypto
function it may not have been destroyed.
There's a plethora of crypto machines designed to encrypt/decrypt
teletype transmissions. That's an area that I'm interested
in, but not one where I have a collection of equipment.
The most interesting one of those is the KW-7 Orestes (
Jerry Proc) &
KL-7
Adonis. That's because I worked for TRW Microwave at
the time the book "Falcon and the Snowman" (
Wiki,
IMDB,
Amazon)
came out. Also the John Walker Family Spy ring (
Wiki)
caused the Pueblo to be captured so the Soviets could get these
machines.
Harris KGV-72
Would use the Sierra II' crypto chip which is the basis of all the
Type 1 cryptography. But this is a new empty box.
KG-84
Wiki "The KG-84A
and KG-84C are encryption devices developed by the U.S. National Security Agency
(NSA) to ensure secure transmission of
digital data. The KG-84C is a Dedicated Loop Encryption Device
(DLED), and both devices are General-Purpose Telegraph
Encryption Equipment (GPTEE). The KG-84A is primarily used for
point-to-point encrypted communications via landline, microwave, and satellite systems. The
KG-84C is an outgrowth of the U.S. Navy high frequency (HF)
communications program and supports these needs. The KG-84A
and KG-84C are devices that operate in simplex, half-duplex, or full-duplex modes.
The KG-84C contains all of the KG-84 and KG-84A modes, plus a
variable update counter, improved HF performance, synchronous
out-of-sync detection, asynchronous cipher text, plain text,
bypass, and European TELEX protocol. The KG-84 (A/C) is
certified to handle data at all levels of security. The KG-84
(A/C) is a Controlled
Cryptographic Item (CCI) and is unclassified when unkeyed. Keyed KG-84
equipment assumes the classification level equal to that of
the keying material used."
Installation Parts
AC Power Cord

|
KG-84 Circular to DB-25 Red/Black Adapter
Box

|
KG-84 Circular to DB-25 Red/Black Adapter
Box Open
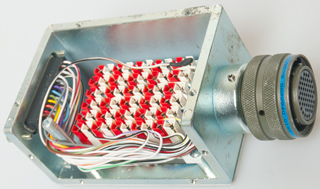
|
U-229 - DB-9 Crypto Fill Cable

|
KG-84 Circular to DB-25 Red/Black Adapter
Cable

|
|
Unknown application.
Fill (aka Key Loader)
There are a number of different things that can be
filled.
Wiki: Glossary of cryptographic keys, Fill Device
- a SINCGARS or Have Quick hop set telling the radio what
frequencies are allowed for frequency hopping.
- a SINCGARS or Have Quick lockout set telling the radio what
frequencies not to use.
- a SINCGARS or Have Quick Transmission Security Key (TSK)
telling the radio the order to do the hopping.
- a KY-57 or ICOM Transmission Encryption Keys (TEK) for the
voice/data encryption unit
- a KY-57 or ICOM Key Encryption Key (KEK) used for Over The
Air Rekeying (OTAR)
- a GPS Group Unique Variable (GUV) key good for one year
- a GPS Crypto Variable Weekly (CVW) good for 6 weeks
- There are probably many more different keys used for data
(teletype) and for trunked phone systems that may be the same
as the above or different.
Historical
Key Fill Devices (KFD)
There are two electrical formats
for key fill. DS-101 (the newer of the two protocols) like
used with the CYZ-10 and DS-102 like used with the old KOI-18
paper tape reader.
I think the DS-102 uses six volt levels working from ground to a
negative potential whereas the DS-101 uses TTL (zero and +5 V)
levels (RS-485).
Note there are many key types (Wiki:
List
of
cryptographic key types,
Key Size) and
the fill device needs to be able to handle the desired keys.
2019 October 22: Computer Business Review: EXCLUSIVE –
Last
Punched Tape Crypto Key Rolls off the NSA’s Machines -
KOI-18 5810-01-026-9620 Tape
Reader General Purpose
DS-102 protocol. The KOI-18 may be the oldest
electrical key loader (the KY-38 used a
mechanical key loader). Used to load the Transmission
Encryption Keys (TEK) into the KY-57
and about anything that needs a key. It uses a
photo optical reader to read a paper tape that's pulled
through the reader by hand.
Very versatile since what comes out depends on what is punched
on the tape. Other key loaders have electronic registers
that can only hold keys in predetermined formats.
Manuals: TM 9-1425-429-12 or TM 9-1425-2586-10
TM 11-5810-292-13&P
Battery: 6.3 Volt BA-5372/U (used to be the 6.5 Volt Mercury
BA-1572/U)
Supports 128 bit keys (actually any length paper tape that
someone can pull through the machine)
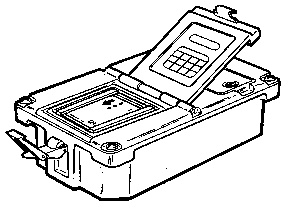 |
 |
Fig 10

|
Fig 12
 |
Fig 13 8-level tape (Wiki)
is 1" wide.

|
Fig 14 Note grouped as 3-space-5.
The space is where the sprocket holes are.
 |
Fig 15 The rod with the blue tape seems
to be made of carbon and is the common ground for the
wire fingers that sense the 8 data holes. Note
there is no sensor for the sprocket holes.
 |
|
|
TM 11-5810-292-13&P General Purpose Tape Reader, KOI-18;
Elect Transfer Device, KYK-13; Net Control Device, KYX-15/15A
I've heard that it uses 8 level ASCII type tapes rather than
the older 5 level Baudot tapes. Note that the data holes
are larger in diameter than the sprocket (clock) holes.
This is important since the leading edge of the sprocket hole
can be used to latch the data bits and the trailing edge of
the sprocket hole can be used to shift out the data
bits. This would not work if all the holes were the same
diameter.
In the old mechanical tape readers, like on the
Teletype Corp. Model ASR33 machine, there was a plastic
wheel with pins that match the sprocket holes and it pulled
the tape through a reader that worked using mechanical pins
to sense each data hole.
Inside there's probably a parallel in - serial out shift
register. The parallel inputs are driven from the data
holes. The shift register data is latched on the rising edge
of the sprocket hole and on the falling edge a pulse generator
sends 8 clock pulses which are used both to clock out the
shift register data bits and to provide the clock signal to
the device being loaded. The clock rate needs to be fast
enough to get all the bits sent before the next set of holes
gets to the tape reader.
If the tape was pulled at 3 feet per second and the pitch of
the data was 0.1" then there would be 360 words per second (8
bits per word) or an average rate of 2,880 bits per second, so
the internal clock generator needs to run faster, say 5,000
bits per second.
If the operator pulls the tape too fast the bits will get
corrupted. To check for this the tape needs to be
punched with parity, Cyclic Redundancy Check (CRC), check sum
or some other data to be sure the correct key gets
loaded. This is not a part of the key loader, but
instead is part of how the data is punched into the tape. This
check can also be used by the the device holding the key to
tell the difference between no key and a valid key. The
device being loaded should not function without a valid key
and it's cold start state should be such that it is recognized
as a no key state. For this reason even parity is not a
good way to go because a key of all zeros would have even
parity. If odd parity is used a key of all zeros fails a
parity test.
Note that an asynchronous data system, like RS-232 that uses
start and stop bits will not work with a hand pulled paper
tape reader because the baud rate can vary over a huge
range. This is why a synchronous system is used that has
data and clock channels. Newer key loaders that are not
paper tape based continue to use the data plus clock format
for backward compatibility.
"COMSEC equipment
description
General purpose tape reader, KOI-18/TSEC, controlled
cryptographic item (CCI).
The National Security Agency (NSA) has directed that a
fill cable be connected to the fill device when
transferring a key.
KOI-18 tape reader, general purpose.
(a) Battery operated, hand-held device.
(b)Converts eight-level standard paper and mylar tape to
serial electronic information.
(c) Loads keys from prepunched tape to other COMSEC
equipment, KYK-13 or KYX-15.
(d) Has no storage capability.
(e) Tapes are normally generated ahead of time and stored
for later use. May be distributed by mail or
courier."
There is no limit to the key size since it will just read
whatever is on a tape.
There are two very major problems with this system.
First the amount of key material is gigantic and the logistics
of getting the keys where they need to be is a huge
task. Because the keys need to be made at NSA well
before they are used they are vulnerable to being copied or
compromised anywhere along the path to the end user.
This has happened more than once during the cold war.
One attempt has been made to secure the key tape between it's
generation and use is a canister that claims to prevent
returning a key tape.
4108390
Paper tape canister, Hugh V. Hayes, Secretary Of The Army,
Aug 22, 1978,
242/588.6, 242/615.3, 225/52 -
4768693
Canister opener, James E. Tomaszewski,
Sep 6, 1988, 225/94, 30/363, 30/120.3, 380/59 -
to allow inspection prior to disposal
The KLL -1 is a more modern version
of the KOI-18 made in Germany. (Crypto Museum: KLL-1)
KYK-13 5810-01-026-9618
Electronic Transfer Device
Fig 0
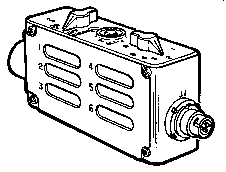
|
Fig 1

|
Fig 2
 |
Fig 10
 |
Fig 11 UV flashlight
 |
|
DS-102 protocol. This electronic key device
looks very similar to the MX-18290 and is
designed to hold TEKs and so replace the KOI-18. THe
KYK-13 is smaller than the MX-18290.
Uses the common crypto battery BA-5372/U.
Holds 6 TEK variables.
20 Aug 2004 - there is some confusion about what key size the
KYK-13 can hold. The PLGR can use the
KYK-13 to load its GPS key which is 128 bits long. But
other references say the KYK-13 can only hold a 64 bit
key. I think it's 128 bit keys.
Instructions for loading key from paper tape (KOI-18) into KYK-13:
1. Connect the LOI-18 to the KYK-13.
2. Turn the KYK-13 selection knob to the desired buffer.
3. Open the latch on the LKOI-18.
4. Insert the paper tape (printed side up) into the slot
marked IN.
5. Turn the KYK-13 command knob to ON.
6. Push the load INIT switch on the KYK-13.
7. Pull the paper tape thorough the KOI-18.
8. Turn the KEY-13 command knob to OFF.
9. Press the load INIT switch on the KYK-13. If the key
was loaded successfully, the load indicator light on the
KYK-13 will flash. (same as when loading a key into user
equipment)
10. If more keys are needed to be loaded, turn the selection
knog on the KYK-13 to the desired buffer, and startr again at
step 3.
KYX-15
5810-00-026-9619 Net Control Device
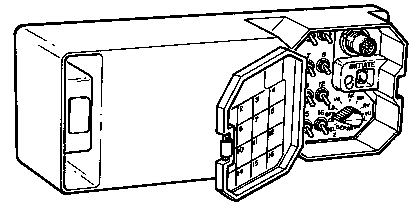
DS-102 protocol. Don't have much info in this Net
Control Device, but it can load a TEK.
Powered from a BA-5372/U
Does support KY-57. See
TM 11 5820-890-10-3 pg 102 (3-20).
TM 11-5810-292-13&P
KYX-15A 5810-01-095-1312 Net Control Device
TM 11-5810-292-13&P
Probably can hold different types of predefined
variables and can load more than one variable because a switch
allows selection of those that need to be loaded. This
would make loading all the different variables into a modern SINCGARS radio
much easier that with the above key loaders.
The VG switch position may mean Crypto Net Variable
Generation, so this device actually generates a key.
Used to load all the KY-57's on a SINCGARS radio net.
It must support 128 bit keys.
Fig 10 Small black and white wires
that have been cut as part of de-mill process.

|
Fig 11
 |
|
|
Local Key Generation
Note that local key generation is a revolutionary
concept. All prior keying methods depended on
distribution of keys that were centrally generated. The
problem with that is a spy (Walker
Family
for example) that gains access to the unused keys can
comprise the whole system. In order to generate local
keys requires a high quality hardware random number generator
based on a noise diode or some other physical noise mechanism,
not on any software algorithm. When a network of SINCGARS radios have their keys
loaded using Over The Air Rekeying (OTAR) from the KYX-15()
you know that the keys have not been compromised.
9 Switch positions:
- SEL-Z to zero selected slots
- OFF/CK for power OFF and for ChecKing a slot to see if
it holds a valid key,
- LD for LoaDing a key into the KYK-15 or from the KYK-15,
which direction depends on which device has it's initiate
"load me" button pressed,
- VG for Variable Generation,
- AK for Auto Keying of a remote variable slot that holds
a valid key,
- MK for Manual Keying a remote variable slot that is
either empty or holds an obsolete key,
- RV for Remote Variable for filling the KYK-15 from a
remote source over a radio, (same as RV on KY-57)
- VU for ?
- ALL for zeroizing all slots (with manual lock button)
Nice Photos of
a KYX-15
AN/CYZ-10 5810-01-343-1194 Data
Transfer Device
 DS-101
Protocol. Data Transfer Device (aka ANCD, aka "Crazy 10")
that holds all the keys needed for the SINCGARS and also holds
Standard Operation Instructions (SOI).
DS-101
Protocol. Data Transfer Device (aka ANCD, aka "Crazy 10")
that holds all the keys needed for the SINCGARS and also holds
Standard Operation Instructions (SOI).
Battery: DL123A, U9VL EMER ONLY, BA-3090/U -
this is the very common 3 volt 123 photo battery.
Supports 128 bit keys.
This is the newest variable loader and it can hold all the
different key formats now used and other stuff. It's
internal clock is not good enough to set the time in a
frequency hopping radio like the SINCGARS or Have Quick
radios, not because of dropping battery voltage, but because
it uses a crystal oscillator. All crystal oscillators
change frequency with aging, temperature, power supply
voltage, and other factors.
SINCGARS Fill cable is CX-13467, NSN 5995-01-379-9689.
Note that the SINCGARS needs a number of different fills for
both frequency hopping and for transmission security.
It's not clear if the Crazy 10 supports key generation.
If not it needs a modification to support key generation.
The Crazy 10 uses 3 each common 123 photo batteries (aka
BA-5123/U) in a battery adapter (NSN 5810-01-348-3147) that
has standard "9 Volt" battery snaps. This way a common 9
Volt battery can be used if the 123 batteries are not
available. But the common 9 Volt battery has only 0.6 AH
compared to the 1.4 AH of the 123 battery. Also the cold
temperature performance of common 9 volt batteries is very
poor at and below freezing where the 123 battery is still
going strong.
PS
Magazine
#571
pgs 48-51 - Beating the Battery Blues.
TB 11-5810-394-12 Generic Equipment Information and
Instructions for the AN/CYZ-10 V3 (NSN 5810-01-393-1973) Data
Transfer Device (DTD)
TM 5820-890-20-2 Chapter 6 Fill Devices
TB 5820-890-12 Operator and Unit Maintenance for AN/CYZ-10
Automated Net Control Device (ANCD) NSN: 5810-01-343-1194
(EIC: QSU) with the Single Channel Ground and Airborne Radio
Systems (SINCGARS)
AN/PYQ-10
This is the replacement for the
CYZ-10. Looks sort of like a hand held
PDA. It would be interesting to
learn how good it's internal clock is. i.e. can it be
used to set the date and time or is a seperate GPS still
needed? Ans: the PYQ-10 clock is the same as the Crazy-10
clock. Too bad they didn't improve it. I think I
know how to make a 1,000 times improvement for a small amount
of money.
Key Length
from a now turned off Navy
web
page.
The KG-40A is a mandatory modified version of the
older KG-40, which incorporates variable fill capability. The
modification entails replacement of a printed circuit board
(motherboard) and the front panel assembly. The KG-40A
provides enhanced security using an improved cryptographic
algorithm and electronic key capability. Because the KG-40A
key is a standard 128-bit key, it can only be keyed by the
AN/CYZ-10 Data Transfer Device (DTD) or a KOI-18 Common Fill
Device (CFD). It cannot accept key from the KYK-13 Electronic
Transfer Device (ETD) or from the KYX-15 Net Control Device
(NCD). The KG-40A is an UNCLASSIFIED controlled cryptographic
item (CCI) when unkeyed and is interoperable with the KG-40.
When the KG-40A is keyed, classification equals that of the
key installed.
(BC - note the KYX-15 above is the no change version, probably
the KYX-15A does support 128 bit keys.)
CRC & other
ways to confirm the Key loaded correctly
There needs to be a way for the
device that's holding the key to know that the key has been
loaded without errors and maybe that it's the proper type of key
for that device. For example there are a number of
different devices that use keys of the same length.
Loading a valid key for device "A" into device "B" might not be
correct.
The first test parameter would be the overall length of the key,
i.e. some number of bits. The next in terms of simplicity
would be a parity check, i.e. is the sum of the "one" bits in an
8 bit byte or a 16 bit word even or odd. Note that a key
of all zeros or all ones, like would be there at first power up,
has even parity, so using odd parity will tell you that there's
something there other than an all zero key.
The next level of checking would be a Cyclic Redundancy Code (
Wiki).
This is a check to be sure that there are no single bit (or more
depending of the details of the particular CRC used) errors in
the key. It's appended to the end of the actual key.
A
Painless Guide to CRC Error Detection Algorighims Index V3.00
(9/24/96) -
Cyclic
Redundancy
Check (CRC) -
A feature of some CRC methods is that you can append zeros onto
the input data and run the algorithm to get the CRC bits which
are then used to replace the zeros. Now when the block
that includes the data and appended CRC bits is run through the
algorithm the result is a zero byte.
It may be the case that instead of filling the to be determined
CRC location with all zeros you can fill it with any number and
get that number when running the CRC on the data plus CRC.
For example if placing zeros results in a zero CRC result,
placing 1 might result in a 1 CRC result. If that works
then you could have 256 different CRC flavors if the CRC was a
single byte. These could be used to identify the type of
data the key contains, for example is it a voice security key or
is it a GPS key, how long is the key good, etc.
Over The Air Re-keying (Wiki: OTAR)
aka SAVILLE Automatic Remote Keying (SARK)
The
KY-57,
SINCGARS and a number of other
systems support the OTAR concept. The key being sent is
encrypted with a Key Encryption Key (KEK) with equal to greater
security than the key it's encrypting. The encrypted key
(the black key) is sent over the air. Although anyone may
receive the black key it does them no good without knowing the
KEK. The receiving equipment decrypts the black key into a
usable red key inside the equipment. End use crypto
equipment is designed in such a way that you can not get the red
key as an output. Fill devices are designed to load but
not unload red or black keys.
In the NSA paper
A
History of U.S. Communicatios Security (Vol 1 1973 and 2
1981), the David G. Boak Lectures, NSA (pg 113)
there is a little discussion about SAVILLE Automatic Remote
Keying (SARK). SAVILLE is part of the keying system
implemented in the
KY-57 which was the
first equipment to have this capability. There are two
schools of thought as to why it was done. One is that it
was done to solve the huge logistics problem of supplying the
needed key material. The other is that it was done to
reduce the occurrence of keys that get to the enemy, for example
John Walker (
Wiki).
A problem with OTAR (aka: SARK) was that the military had been
trained to not leave active (keyed) equipment unattended or not
locked up, so it was common for users of the KY-57 to zeroize
the box at the end of each day. That means there must be a
nearby key fill device to reload it the next day. So
operationally it really didn't pan out.
The
DAGR GPS receiver has OTAR
capability but with a new twist. It has a unique
Electronic Serial Number (ESN) like a cell phone. The DAGR
is only classified to the level of the key that it's holding so
a DAGR without a key is not classified allowing it to be
supplied without all the red tape that hardware classification
entails. It is however a Controlled Cryptographic Item
(CCI) and must be accounted for. This appears to be a
solution to the OTAR problem since the crypto variables could be
remotely erased from a unit that was unaccounted for or was
known to be stolen or captured.
But if the designers of the DAGR had been a little cleaver they
would include a low power transmit capability in the DAGR which
can only be activated from the GPS. The signal would be a
spread spectrum signal, similar to the GPS signal, but not
interfere with GPS and could be received by either the GPS
satellites or some other ELINT type satellites. An
analysis of the
Black Box showed
that this is very possible. This way a stolen receiver
could be queried and report it's position, sort of like
Lojack
(
Wiki).
The use of ESNs in crypto equipment has obvious benefits so I
expect it's already being done.
Red & Black Keys
Red Keys
When a Red key is combined with it's crypto system the plain
text information is accessible. Since the cipher text and
the crypto systems are in the public domain the Red key needs to
be well controlled to protect the information. There are
two major problems associated with protecting Red keys.
First, it takes a long logistics chain to supply authorized
users with the keys they need. That long logistics chain
causes the second reason, the Red keys are prime targets of
spies. An example is the Walker Spy Ring (
Wiki).
In addition to the Red key itself there is also how the key is
handled in hardware. If the Red key or data can be tapped
in the hard ware then it still may be captured. For
example GPS receivers with the Precision Positioning Service -
Security Module (PPS-SM) such as the
SLGR
or
PLGR process the Red key and output
plain text to the rest of the receiver. That plain text
could be tapped and recorded allowing someone to then key other
like GPS receivers.
Black Keys
Black keys are Red keys that have been encrypted with a Key
Encryption Key (KEK). Black keys can be freely distributed
and even transmitted over radio channels. The use of black
keys solves some of the problems of Red keys. My
grandmother had a saying "Don't put all your eggs in one
basket". The idea is that if the basket is dropped
you loose all the eggs. The analogy being if the enemy
somehow gets the KEK then all of the Black keys can be turned
into Red keys.
But if the crypto equipment converts the black key into a red
key or into plain text information then capturing keyed
equipment opens the door to getting all the plain text in the
system.
If the hardware does not expose the red key or plain text then
the use of black keys is much more secure. That's probably
the main reason the PPS-SM is being replaced with the Selective
Availability/Anti-Spoofing Module (SAASM) (
Wiki).
Electronic Serial Number (ESN)
The DAGR GPS receiver also has an Electronic Serial Number
(ESN). The ESN is hidden in the SAASM hardware chip (not
like a cell phone where it can be forged). This
allows messages specific to that GPS receiver to be sent.
I'm guessing it's similar to an IP address. If so then
black keys could be sent to a group of GPS receivers from the
GPS satellites. The problem I see with doing it is there
needs to be some way that you know all the receivers being
re-keyed are in the possession of authorized personnel. If
that's not done then there's a chance you will be
re-keying a unit in enemy hands. Also you probably can
erase all the currently loaded keys.
Fill Hardware
The modern crypto equipment no
longer uses punched cards but the KOI-18 paper tape reader is
still the most versatile in terms of supporting various key types
since it does not have any built in protocol dependencies.
The two serial fill protocols are DS-101 and DS-102. Neither
of the specs are in the public domain.
DS-101 is based on RS-232 (asynchronous, i.e. just bipolar data
and ground, no clock).
DS-102 is based on a negative polarity key fill protocol that uses
a data and clock line.
Not used for voice security.
CV4228 PC to SINCGARS Fill Cable
Fill Cable - not sure, but
probably.
NSN 5810-01-066-7587 is an official fill cable.
SINCGARS W4 Cable
Some of the SINCGARS manuals refer
to the W4 as an Audio/Data/Fill cable. It's wired 1:1 on 6
contacts of the AUDIO connector.
Taking a look at how this connector is used for:
Audio, Fill, Data and Retransmission.
For the destruction of paper or
plastic key tapes
Test Equipment
USM-481 VINSON Interconnect Test
Set
Used to check the cables and
junction boxes in a VRC-12 series vehicle installation.
Used to measure the Bit Error Rate
of a channel where VINSON will be used.
Hardware Random Number Generator
An idea would be to use a diode
noise source and after amplification drive a PIC micro
controller. The PIC would look at two successive data bits
and if they were the same get two more. If the input was
10 a 1 bit would be shifted into a byte, if the input was 01 a 0
bit would be shifted into a byte. When the byte was full
it would be stored and after say 8 or 16 bytes were stored they
would be sent out an RS-232 data port. By using the noise
diode and NOT using an algorithm the numbers would be nearly
random. But using the simple algorithm described any bias
is removed and the resulting data stream is truly random.
A refinement would be to take the 8 or 16 bytes and pass them
through something like the Tiny Encryption algorithm to really
mix them up. But it's not clear that this really buys
anything when compared to the simple way.
hardware
white
noise generator -gain of 1000 x voltage following a noise
source drives the digital input of a PIC microcontroller.
Algorithms & Protocols
An algorithm is how you get from
plain test to the cipher text. They are categorized by how secure
they are with Type 1 being the best.
NSA encryption algorithms (
Wiki)
A protocol has to do with the layers below the algorithm down to
the physical layer.
Cryptographic protocols (
Wiki)
For example the KY-57 Voice Encryption unit is a Type 1 product
that makes use of the SAVILLE algorithm (
Wiki 128 bit
key). It's a member of the VINSON family of products that
can interoperate which includes the KY-57, KY-58, KY-68, KY-99a,
KY-100, KYV-2,
FASCINATOR and SINCGARS or other
radios with embedded VINSON capability.
Type 1 NSA Certified cryptographic algorithms include:
a) BATON/MEDLEY,
b) SAVILLE/PADSTONE;
c) KEESEE/CRAYON/WALBURN;
d) GOODSPEED;
e) ACCORDION;
f) FIREFLY/Enhanced FIREFLY; and
g) JOSEKI Decrypt. (
Wiki) - a way to
encrypt/decrypt computer programs
Type 2 cryptographic algorithms for use in communications systems
endorsed by NSA. These include classified algorithms.
Type 3 cryptographic algorithms for Sensitive but Unclassified
information include:
a) DES, Triple DES;
b) AES;
c) Digital Signature Standard (DSS); and
d) Secure Hash Algorithm (SHA).
Exportable Type 4 cryptographic algorithms are Registered with
NIST but not FIPS.
Key Management
List of cryptographic key types (
Wiki)
a) SARK/PARK (KY-57, KW-5 and KG-84
MC OTAR);
b) DS-101 and DS-102 Key Fill;
c) SINCGARS Mode 2/3 Fill;
d) Benign KeylBenign Fill.
Links
Back to Products made by Brooke, Crypto, Crypto
Patents, Military Audio, Squad Radio, Military
Information, Home page
Page created 14 Dec 2002.
---------------------
Place holder for Crypto.shtml
NYTBook Review by David Kahn, Dec. 29, 1974: The
Ultra Secret -






























 DS-101
Protocol. Data Transfer Device (aka ANCD, aka "Crazy 10")
that holds all the keys needed for the SINCGARS and also holds
Standard Operation Instructions (SOI).
DS-101
Protocol. Data Transfer Device (aka ANCD, aka "Crazy 10")
that holds all the keys needed for the SINCGARS and also holds
Standard Operation Instructions (SOI).